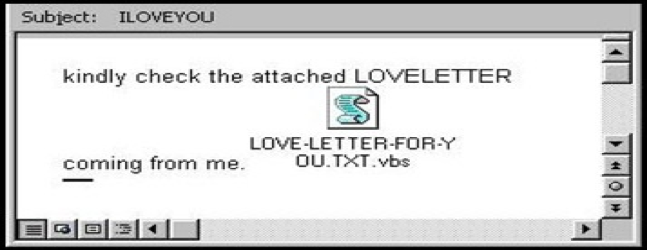
What is republic Act no. 10175?
REPUBLIC ACT NO. 10175.
It is a Cyber-crime providing for the prevention , investigation suppression and the imposition of penalties therefor and for other purposes.
How many chapters does it contain? enumerate each chapter with its corresponding title?
THE
REPUBLIC ACT NO.10175 IT CONTAINS 8 CHAPTERS
Chapter I Preliminary Provisions
- Section 1. Title
- Section 2. Declaration
of Policy
- Section 3. Definition
of Terms
Chapter II Punishable Acts
- Section 4. Cybercrime
Offenses
- Section 5. Other
Offenses
- Section 6. All
crimes defined and penalized by the Revised Penal Code
- Section 7. Liability
under Other Laws
Chapter III Penalties
- Section 8. Penalties
- Section 9. Corporate
Liability
Chapter IV Enforcement and Implementation
- Section 10. Law
Enforcement Authorities
- Section 11. Duties
of Law Enforcement Authorities
- Section 12. Real-Time
Collection of Traffic Data
- Section 13. Preservation
of Computer Data
- Section 14. Disclosure
of Computer Data
- Section 15. Search,
Seizure and Examination of Computer Data
- Section 16. Custody
of Computer Data
- Section 17. Destruction
of Computer Data
- Section 18. Exclusionary
Rule
- Section 19. Restricting
or Blocking Access to Computer Data
- Section 20. Noncompliance
Chapter V Jurisdiction
Chapter VI International Cooperation
- Section 22. General
Principles Relating to International Cooperation
Chapter VII Competent Authorities
- Section 23. Department
of Justice (DOJ)
- Section 24. Cybercrime
Investigation and Coordinating Center
- Section 25. Composition
- Section 26. Powers
and Functions
Chapter VIII Final Provisions
- Section 27. Appropriations
- Section 28. Implementing
Rules and Regulations
- Section 29. Separability
Clause
- Section 30. Repealing
Clause
WHAT DOES CHAPTER 1 SECTION 1 OF RA 10175 CONTAIN?
Chapter 1 Section 1 Contains all about Act shall be known as the “Cyber-crime Prevention Act of 2012″. It’s officially recorded as Republic Act No. 10175 and it is a law in the Philippines.
WHAT IS DECLARATION POLICY OF RA 10175?
The declaration policy of RA 10175 this is the State recognizes the vital role information and communication industries such as content production telecommunication, broadcasting electronic commerce, and data processing, in the nation’s overall social and economic development.
WHAT IS THE PUNISHABLE ACT OF RA 10175?
A. Offenses against the confidentiality, integrity and availability of computer data and systems:
- Illegal Access
- Illegal Interception
- Data Interference
- System Interference
- Misuse of Devices
- Cyber-squatting
B. Computer-related
Offenses:
- Computer-related Forgery
- Computer-related Fraud
- Computer-related Identity Theft
C. Content-related Offenses:
- Cybersex
- Child Pornography
- Unsolicited Commercial Communications
- Libel.
IF FOUND GUILTY, WHAT ARE THE
PENALTIES?
This is the penalties when the
person found guilty. Any person found guilty of any of the punishable acts
enumerated in Sections 4(a) and 4(b) of this Act shall be punished with
imprisonment of prision mayor or a fine of at least Two
hundred thousand pesos (PhP200,000.00) up to a maximum amount commensurate to
the damage incurred or both.
Any person found guilty of the
punishable act under Section 4(a)(5) shall be punished with imprisonment of
prision mayor or a fine of not more than Five hundred thousand pesos
(PhP500,000.00) or both.
If punishable acts in Section
4(a) are committed against critical infrastructure, the penalty of reclusion
temporal or a fine of at least Five hundred thousand pesos
(PhP500,000.00) up to maximum amount commensurate to the damage incurred or
both, shall be imposed.
Any person found guilty of any of the punishable acts enumerated in Section 4(c)(1) of this Act shall be punished with imprisonment of prision mayor or a fine of at least Two hundred thousand pesos (PhP200,000.00) but not exceeding One million pesos (PhPl,000,000.00) or both.
DO YOU THINK RA 10175 IS ENOUGH TO PROTECT THE COUNTRY AND CITIZENS AGAINST VARIOUS CYBER CRIMES?
I think being protect the country and the citizens against the various cyber crime is not fully enough to protect and to help people but because of this act they deliver to help the country and the citizens to avoid in a critical way of condition for being involve the incident. In Philippines is the center of the many involve people for the victim of a crime half of it want a justice for being protected by the RA 10175 they want to a peaceful justice from bringing they self in a critical way but RA 10175 is the one to help people to being protected in a good way but the other half they can’t assure to handle because of the country are populated of a committing a crime they can’t predict the other side of people who can do the crime to the country and the innocent citizens.
REFERENCES: https://www.lawphil.net/statutes/repacts/ra2012/ra_10175_2012.html